#c++ postfix
Explore tagged Tumblr posts
Text
/disagree
There is no interpretation of the problem-as-stated-by-op where "add 1" is the complete solution.
OP says to do this operation on "an integer"
It cannot mean "the platonic model of an integer" because those have no bits and also cannot be represented in digital logic e.g. the integer might be Graham's Number.
It also cannot mean "keyword integer" because C doesn't have that keyword.
it could mean "keyword int." Probably not - OP uses "uint32_t" but it could. In that case, adding 1 to 0xFFFFFFFF is undefined behavior.
it could mean "machine word integer" which is more probable given the use of "uint32_t" as the input. The machine word integer does not have a carry bit.
BUT
PLAYING with the IDEA that you should always increment by 1, the correct implementation does not use c++, it uses ++c:
a = c++; -> No. a does not contain the value as specified.
a = func(c) where func(c){return c++;} -> No. a does not etc./
a = ++c; -> No. a correct, but c modified and spec "a function" not implemented.
a = func(c) where func(c){return ++c;} -> No. Correct implementation of functional requirement, weird implementation of default nonfunctional requirement "perf" (assembly different from "return c+1")
a = func(c) where func(c){return c+1;} -> Correct.
Godbolt
"But that's in debug mode turn on the optimizer" what you think you can get away with writing bad code just because your clients can optimize? What if they're running in debug mode to find your weird off-by-one mistake?
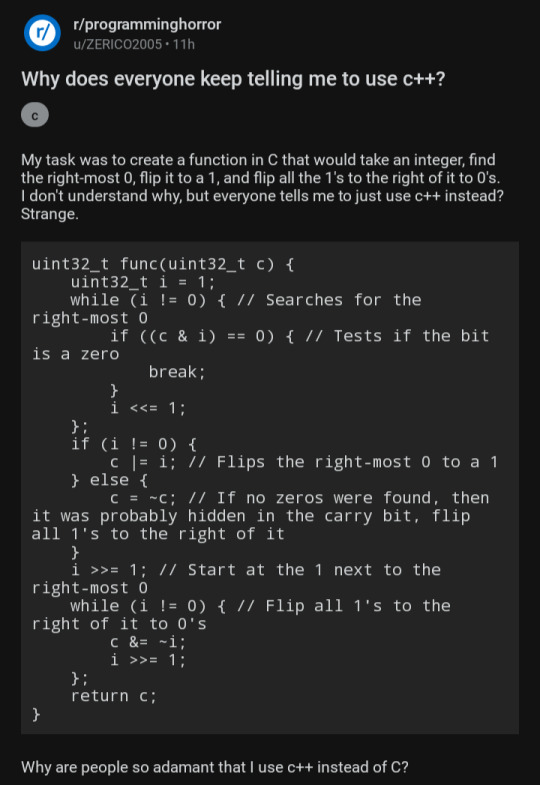
[Source]
#I legitimately did not get that “use c++” wasn't about the language#when I originally saw this post#because operator-postfix-increment is the wrong solution for 3 different reasons#it did not even occur to me it could mean anything BUT “change language.”
170 notes
·
View notes
Text
CSCI 689 Computer Assignment 9
Write a C++ program that implements a simple arithmetic calculator. Input to the calculator consists of lines composed of real numbers combined together using the arithmetic operators and The arithmetic expressions in input lines are given in postfix forms, which eliminates the need of using parentheses. You can use a container (of type ) to evaluate a postfix expression. The routine defines an…
0 notes
Text
Basic Spelling Rules Explained
You can instruct yourself to be a superior speller. Realize that figuring out how to spell is a procedure that is never finished. Spelling is something that everybody needs to focus on and continue working at it.

Fundamental SPELLING RULES
Short-Vowel Rule: When one-syllable words have a vowel in the center, the vowel more often than not has a short stable. Models: feline, hound, man, cap, mother, father, got. In the event that the letter after the vowel is f, l, or s, this letter is frequently multiplied. Models: staff, ball, pass.
Two-Vowels Together: When two vowels are by one another, the primary vowel is normally long (the sound is equivalent to the sound of the letter) and the subsequent vowel is quiet. Models: meat, situate, plain, downpour, goat, street, lie, pie.
Vowel-Consonant-e Pattern: When a short word, or the last syllable of a more extended word, finishes in this example vowel-consonant-e, at that point the principal vowel is typically long and the eis quiet. Models: place, cake, mice, vote, quiet.
Y as a long I: The letter y makes the long solid of I when it comes toward the finish of a short word that has no other vowel. Models: cry, attempt, my, fly, by, hello.
Y as a long E: When y or ey closes a word in an unaccented syllable, the y has the long solid of e. Models: cash, nectar, many, key, clever.
I before E: Write I before e when the sound is long e aside from after the letter c. Models: alleviate, help, respite. At the point when there is a c going before, at that point it is ei : receipt, get, roof, mislead, consider.
E before I: Write e before I when the sound is long a. Models: weight, cargo, rule. Another approach to recollect this is: "I before e with the exception of after c, or when seeming like an as in neighbor and gauge." When the ie/ei mix isn't articulated ee, it is normally spelled ei.
Oi or Oy: Use oi amidst a word and use oy toward the finish of a word. Models: bubble, soil, drudge, kid, toy.
Ou or Ow: Use ou amidst a word and use ow toward the finish of words other than those that end in n or d. Models: mouse, house, discovered, mount, get, push, toss, crow.
Twofold Consonants: When b, d, g, m, n, or p show up after a short vowel in a word with two syllables, twofold the consonant. Models: bunny, way, blade, pennant, drummer.
The ch sound: At the start of a word, use ch. Toward the finish of a word, use tch. At the point when the ch sound is trailed by ure or particle, use t. Models: pick, champ, watch, get, picture, delight.

Postfix AND INFLECTION RULES
Words finishing with a quiet e: drop the e before including a postfix which starts with a vowel: state, expressing; like, loving.
Keep the e when the postfix starts with a consonant: state, explanation; use, helpful.
At the point when y is the last letter in a word and the y is gone before by a consonant: change they to I before including any postfix aside from those start with y: magnificence, lovely; sear, fries; woman, women.
When framing the plural of a word which finishes with a y that is gone before by a vowel, include s: toy, toys; monkey, monkeys.
At the point when a one-syllable word finishes in a consonant gone before by one vowel, twofold the last consonant before including an addition which starts with a vowel. This is additionally called the 1-1-1 rule, i.e., one syllable, one consonant, one vowel! Model: bat, batted, batting, hitter.
At the point when a multi-syllable word finishes in a consonant gone before by one vowel, and the last syllable is emphasized, a similar guideline remains constant – twofold the last consonant. Models: control, controlled; start, starting.
At the point when the last syllable does not have the end-highlight, it is liked, and at times required, that you NOT twofold the consonant. Models: center, centered; revere, venerated. For more in-depth information about spelling I highly recommend this website Portuguese Spell Checker.
youtube
1 note
·
View note
Text
I mean.. nobody needs caps-lock. You can just upcase-word if needed.
I know some people map it to ESC but C-[ is ESC so ctrl is the better choice there.
Also I never use the Hungarian keyboard layout. I use the latin-2-alt-postfix input mode in emacs to enter Hungarian text. This makes Hungarian people unreasonably angry.
Also nobody needs icons or shortcuts while we're at it. Completing read is such a better solution. This also make people very angry.
i just discovered a new functionality with my computer. holding alt then scrolling will go through previous versions of the page, then scrolling the other way returns to the old ones. didnt mean to write this in the header of this post. anyway why is this a functionality who needs to go back 800x in 2 seconds??
524 notes
·
View notes
Text
The Top Ten Spelling Rules
Realizing spelling rules, and the exemptions to the standard, is an incredible methodology to enable you to comprehend why spelling is how it is and encourages you spell. In this exercise we'll take a gander at the best ten spelling rules.

A few people think on the off chance that they get familiar with a spelling rule they'll have the option to spell. Shockingly, the issue with principles is you need to recollect the standard! What's more, which words work with the standard and the words that don't!
Be that as it may, a few people like learning rules, get a buzz out of discovering how to utilize them. It's in every case great to realize why spelling is the way it, and realizing spelling principles is one of numerous systems to enable you to spell well. So regardless of whether you overlook the standard, possibly you'll recollect the spelling design, and at any rate you ideally will know why a spelling is how it is.
We should take a gander at the best ten standards in an essential manner without any special cases only the stripped down of the standard. On the off chance that you need an increasingly point by point spelling principles course, at that point look at my seminar on udemy.com/spelling-rules-course for my inside and out spelling guidelines course with worksheets and activities.
1. the "I before e aside from after c" rule
accept - get
As a fundamental guideline this is extraordinary
be that as it may, shouldn't something be said about antiquated, relaxation, neighbor/neighbor
We have a more drawn out form of the standard:
" I before e aside from after a long c yet not when c is a "sh" sound and not when seemed like 'an' as in neighbor or gauge."
( I before e rule) accept, accomplish, (aside from after c),receive, roof (however not when c is seemed like sh) old, capable
not when seemed like 'a' ) eight, beige
Be that as it may, there are special cases consistently exemptions so watch out for them.
2. Evolving "y" to "ies"
You probably won't realize the spelling rule however you may realize the spelling design - the vast majority do.
At the point when the word finishes in a vowel + y simply include 's'
key → keys
delay → delays
trolley → trolleys
(since we can't have three vowels in succession delaies x )
In the event that the word has a consonant before the 'y':
remove the 'y' and include 'ies'
child → babies
organization → organizations
trouble → challenges
3. Adding - es to words finishing off with - s, - ss, - z - ch - sh - x
This was added hundreds of years prior to stop the plural 's' conflicting with these letters and it relaxes the 's' sound to a 'z' sound
bus→ transports
business → organizations
watch → observes
box → boxes
test → tests
4. 1:1:1 bending over guideline
put - putting, huge greater, test - tests, swim - swimming...
At the point when a word has one syllable + 1 vowel beside 1 consonant we bend over the last consonant with a vowel addition:
sit - sitter, huge - greatest, tap - tapping, shop - customer/shopping, fat - stuff, swelling, fatter, fattest...
This occurs in longer words when the pressure is on the last syllable:
start (beGIN) - novice, starting
allude (reFER) - alluding, alluded
happen (ocCUR) - happening, happened, event
5. Drop the 'e' rule
We more often than not drop the last quiet "e" when we include vowel postfix endings, for instance:
compose + ing → composing
trust + ed = trusted
energize + capable = edgy
joke - joker
enormous - largish
close - shutting
sense + ible = reasonable
inverse + particle = resistance
envision + ation = creative mind
We keep the 'e' if the word finishes in – CE or – GE to keep a delicate sound, with capable/ous
boldness + ous = fearless
shock + ous = incredible
see + capable = detectable
oversee + capable = sensible
6. Evolving the "y" to "I" when including postfix endings.
On the off chance that a word finishes in a consonant + Y, the Y changes to I (except if including endings with "I" - ing - ish, which as of now starts with an I)
beauty+ful > beauti+ful =beautiful, embellish, beautician
upbeat + ness = - satisfaction, joyfully, more joyful, most joyful
irate + er = angrier, angriest, furiously,
truly: prettier, prettiest however prettyish
prepared: promptly availability
dry: dried, BUT drying, dryish
resist: challenges, opposed, yet resisting
apply: applies, connected however applying
7. "- f" to "- ves" or "- s"
Most words finishing off with "- f" or "- fe" change their plurals to "- ves"
calf - calves
half - parts
blade - blades
leaf - leaves
portion - portions
life - lives
spouse - wives
rack - racks
hoodlum - criminals
yourself - yourselves
A few words can have the two endings - ves or - s:
scarf - scarfs/scarves
overshadow - diminutive people/dwarves
wharf - wharfs/wharves
tissue - hankies/handkerchieves
Words finishing off with - ff you simply add - s to make the plural.
bluff - precipices
toff - toffs
scrape - scrapes
sniff - sniffs
A few words finishing off with - f include - s:
Things which end in two vowels in addition to - f generally structure plurals in the typical manner, with only a - s
boss - boss
parody - parodies
rooftop - rooftops
boss - boss
brute - brutes
Special cases: cheat - criminals, leaf - leaves

8. Words finishing off with - ful
The addition – FUL is consistently spelt with one L, for instance:
grind + ful = thankful
confidence + ful = loyal
trust + ful = cheerful
cautious
accommodating
helpful
thankful
lovely (see the"y" progresses toward becoming "I")
9. Including - ly
When we add - ly to words finishing off with - ful then we have twofold letters
appreciatively
dependably
ideally
We likewise add - ly to words finishing off with 'e'
love + ly = exquisite
like + ly = likely
live + ly = exuberant
complete + ly = totally
unmistakable + ly = certainly
Yet, not genuinely (genuine + ly) This is a typical incorrectly spelled word.
We change the end 'e' to 'y' in these - le words
delicate > tenderly
inactive > inertly
unpretentious > inconspicuously
10. When we include "all" to the start of words we drop the l
all + so = moreover
all + most = nearly
despite the fact that
continuously
god-like
as of now
okay (OK as two words is utilized in increasingly formal English)
out and out (Note that inside and out and all together don't mean something very similar. By and large signifies 'altogether', as in there are six rooms through and through, though all together signifies 'across the board spot' or 'at the same time', as in it was a great idea to have a gathering of companions all together; they came in all together.)
That is it for my main ten principles and It's incredible to thoroughly understand spelling rules. Visit English Online Corrector if you are looking for more Information.
youtube
1 note
·
View note
Text
5 Most Important Spelling Rules
Around Shakespeare's time, when spelling was first getting to be institutionalized, the spelling of most English words was for the most part phonetic—or if nothing else more phonetic than it is today. For instance, English speakers did once articulate the k toward the start of words like blade and knee. Be that as it may, despite the fact that nobody has articulated knee as "kuh-nee" in hundreds of years, regardless we hold tight to the old spelling.
Luckily, there are a couple of general guidelines that can help when you're looked with a word you don't know how to spell.

Spelling Rule 1: I Before E, Except After C
The standard goes this way:
I before E, Except after C, except if it sounds like An, as in neighbor or gauge
There are numerous special cases to this standard—possibly it's smarter to consider it a rule—however it tends to be useful with words like the ones beneath.
I before E
Okay like a bit of cake? Jerry will think anything. They're planting new grass on the football field .
Aside from before C
Darnell got An on his spelling test. Jeremy detected a bug on the roof . I never anticipated such misleading from you!
Except if it sounds like A
Our neighbors live in a beige house. What amount does the little cat weigh ?
Here's a tip: It's a smart thought to remember these basic special cases to the standard:
seize, either, abnormal, tallness, outside, relaxation, soul, fake, relinquish, not one or the other, science, species, adequate
Spelling Rule 2: Adding Suffixes to Words that End in Y
When you include a postfix that begins with E, (for example, - ed, - er, or - est) to a word that finishes in Y, the Y generally changes to an I.
Cry – cried – messenger
Dry – dried – drier
Lay – laid (note the sporadic spelling: no E)
Infant – babies
Family – families
Revolting – ugliest
This is the dustiest old house I've at any point seen. The best bread cooks make the flakiest pie coverings. The soup needs the most minor squeeze of salt, and afterward it's ideal. Seawater dries out your skin.
The Y doesn't change for the addition - ing.
The child has been sobbing for very nearly 60 minutes. The moment we got the new young doggie, our mom started setting down sheets of paper. We ought to invest some energy cleaning before the visitors arrive.
On the off chance that the word being referred to has two consonants before the Y, change the Y to I before including the postfix ‑ly.
Messy – carelessly
Glad – joyfully
Unnerving – scarily
Entertainingly enough, I said something very similar just yesterday.
Obviously, there are consistently special cases:
"Clever," he said dryly .
Spelling Rule 3: The Silent E
Regularly, an E after a consonant toward the finish of a word is quiet, yet it affects the manner in which you articulate the vowel that precedes the consonant. The E makes the vowel sound of the word (or syllable) long (like the I sound in kite) rather than short (like the I sound in cat). It's critical to get the quiet E right, since its essence or nonattendance can change the significance of a word.
The monkey bit me. Keep your fingers out of the pen: the monkeys nibble .
By adding the E as far as possible of bit, the word is changed from past to current state.
Try not to cut yourself on the sharp blades. The cat is extremely adorable .
For this situation, the quiet E makes a totally extraordinary word.
When including an addition like - ed, - er or - est, the quiet E is generally dropped from the finish of the root word.
The pooch exposed his teeth at the mail transporter. The infant's eyes were the bluest I'd at any point seen.
Spelling Rule 4: Double Consonants
Watch out for twofold consonants. It very well may be hard to hear them when a word is said resoundingly—particularly if the word has just a single syllable. Twofold consonants are much of the time found in words that have additions added to them:
I dropped the substantial sacks to the floor. Somebody called for you before.
A few words can be articulated as it is possible that a couple of syllables, however the spelling continues as before:
Favored are the mild for they will acquire basically everything.

In this sentence, which is a fixed articulation, favored is articulated as two syllables: favor ed.
The dad favored his child before the wedding.
In this sentence, favored is articulated as one syllable: blest.
Be especially cautious with words where a twofold consonant can change the articulation and the importance of the word.
Prickly plants are local to the desert . Would you like frozen yogurt for treat ?
Spelling Rule 5: Plural Suffixes
When do you include ‑s and when do you add ‑es to make a plural? It's not exactly as subjective as it might appear. The standard is this: if a word finishes in ‑s, ‑sh, ‑ch, ‑x, or ��z, you include ‑es.
I just needed to take one transport; you needed to take two transports. I just get one wish; you get two wishes. I have a splotch on my shirt; you have two splotches. I'm conveying one box; you're conveying two boxes. OK like a spritz of fragrance? Two spritzes, if it's not too much trouble
For every single other consummation, include ‑s.
I have one feline; you have two felines. I have one cup; you have two cups. I have one shoe; you have two shoes. Where is my other shoe? I have one ski; you have two skis. How am I expected to ski? I have one toque; you have two toques.
Be cautious about words that don't change when they're pluralized (e.g., fish, sheep, moose). In case you're uncertain, check the word reference. If you are looking for more information about English spelling visit English Grammar Corrector right away.
youtube
1 note
·
View note
Text
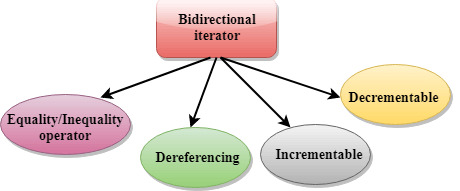
C++ Bidirectional iterator
A Bidirectional iterator supports all the features of a forward iterator, and it also supports the two decrement operators (prefix and postfix).
Bidirectional iterators are the iterators used to access the elements in both the directions, i.e., towards the end and towards the beginning.
A random access iterator is also a valid bidirectional iterator.
Many containers implement the bidirectional iterator such as list, set, multiset, map, multimap.
C++ provides two non-const iterators that move in both the directions are iterator and reverse iterator.
C++ Bidirectional iterator has the same features like the forward iterator, with the only difference is that the bidirectional iterator can also be decremented.
0 notes
Text
here’s my workstation/server to-do list

wait for new cpu and ram
mount new nvme ssd
freebsd (efi boot)
base system on nvme ssd, enlarge /var
/usr and /root on nand ssd
/usr/ports, /tmp and swap on sata hdd
/usr/home mounted on microsd on motherboard
install git, compile and install lynis
drm-kmod, wayland, hikari, alacritty
configure sshd, restrict file system permissions, restrict access to compiler
learn how to use cron, rkhunter, ossec
install tor, nginx, postfix, dovecot, mariadb, php, phpBB, libressl
parse other security recommendations from lynis
set up phpBB and hikari settings
get back to ansi-c programming
0 notes
Text
Deduplicator in mailclient

#Deduplicator in mailclient update#
#Deduplicator in mailclient windows#
This includes several views, contacts merging and much more.ĮM Client includes integrated chat, so you don't need another application for chatting with your friends.
Meeting invitations and confirmations (IMIP/ITIP)Ĭontacts can be managed in many ways in eM Client.
Share calendars and tasks with other people.
Manage your appointments in a beautiful and highly customizable interface
Templates, signatures, tags and categorizations.
Built-in email translator using Bing translate engine.
Follow the prompts in the deduplicator wizard and it quickly eliminates your duplicates. In em client, go to Menu > Tools > Deduplicator. After installing em client, connect it with your Nextcloud instance and let it import your contacts.
#Deduplicator in mailclient windows#
It supports virtually all conceivable email technologies (POP3, SMTP, IMAP, EWS, AirSync). According to their website, there is a Windows and a macOS version. Use your email client easily in a modern way.įind any email, contact or attachment in seconds with eM Client's super-fast search.ĮM Client is the best equipped email client on the market. This includes Microsoft Outlook, Outlook Express, Windows Mail, Windows Live Mail, Thunderbird, The Bat and more.ĮM Client fully supports touch devices like touch-enabled laptops, tablets and hybrid devices. You can easily import your data from most of the other e-mail clients. Quick and easy import from your old email client This is a multi-part message in MIME format.EM Client supports all major services including Gmail, Exchange, iCloud, and You can find more information in the server section. The tool remarkably decreases the size of the Outlook PST files and thus helps in preventing PST corruption due to over-sized. X-Asterisk-CallerIDName: YPCR Braswell EddieĬontent-Type: multipart/mixed boundary="-voicemail_188842702132051636022834" Stellar Deduplicator for Outlook is a useful utility to enhance Outlook performance by removing duplicate emails from the user mailboxes. Convolutional Neural Network (CNN) a Deep Learning algorithm which can take in an input image, assign importance (learnable weights and biases) to various aspects/objects in the image and be able to differentiate one from the other. =?ISO-8859-1?Q?_Braswell_Eddie=22_=3C4109989222=3E?= Image Deduplicator offers a variety of hashing algorithms to find exact duplicates and near duplicates.
#Deduplicator in mailclient update#
Received: (from (8.14.7/8.14.7/Submit) id w11J4RnN023476 kernel for word file repair software crackl, Total Commander Powerpack, tiny duplicator 32 bits, redistribuable visual c++ pour visual studio 2012 update 4, mavis beacon download V 17, downlod source, Free Spider Solitaire 2012 for Windows, Duplicate File, wifi pc file explorer server, diskshare.exe download, 'explorer plus. Ur1H9yJacdGr91EA93TuoEyMJGk+ciw+CJM30RMqb2WO/QL6FtrWItzCk6zwlHnqCNĬD7nnKEiwSj/9E2Hkeh6M0ozNR90TQIRAiGjXXJI= Received: from (.net )īy (Postfix) with ESMTPS id A381530801E8ĭKIM-Signature: v=1 a=rsa-sha256 c=relaxed/simple d= īh=pljnYJnI+JWe2/sJ5Tb/7fXKiJP7PTLtQkk0C4qW79g= ī=GGnpn0rCcz+lbvz0hkx9oW2NqpMCxvbXer3Dah05oHHjUaVEWiKk9SgjY+6xQT6+J Received: from ( )īy (Postfix) with ESMTPS id 6FDF21251DA X-Sieve-Redirected-From: from (localhost )īy (Postfix) with ESMTP id 3ACE91251E3 Received: by (Postfix, from userid 2000) Please run Microsoft Outlook and set it as the. Received: from ()īy ( ) (amavisd-new, port 10024) Either there is no default mail client or the current mail client cannot fulfill the messaging request. Otherwise, copy the information below to a web mail client. Tests=Īuthentication-Results: (amavisd-new) dkim=pass (1024-bit key) We welcome your comments To open the configured email client on this computer, open an email window. X-Spam-Status: No, score=-0.1 tagged_above=-999 required=4 Delivered-To: from (localhost )īy (Postfix) with ESMTP id 363191251D7

0 notes
Text
Xps 15 multitouch

Is no reasons it doesn't load hid-multitouch. At least if udev loads hid-generic, there Before I continue adding the ID all over the > place, including the hid-multitouch.c, could someone shortly comment > about the best, intended place for this - there are so many IDs all > over the place and it is not obvious where it is necessary and where > not. Is this ID for the Surface TypeCover or the XPS 15? I added the ID, > Synaptics, 0x7A13 to the hid-quirks for a test, but this is not yet > probably just add hid-multitouch to some init script, but I wanted to > get it to auto-load liek for my Surface Typecover. Which distribution are you using? and are you running the stock kernel Hmm, if the module is compiled in and you are using udev, there shouldīe no need to manually modprobe the driver. I debugged around a bit > and manually modprobing hid-multitouch appears to bind this to the > hid-multitouch for grearly enhanced functionatliy. > Hi, > I am testing a Dell XPS 15 all-in-one and noticed the I2C connected > touchpad had only very basic mouse function. Subject: Dell XPS 15 multitouch touchpadĬontent-Type: Text/Plain charset=iso-8859-1Ĭontent-Transfer-Encoding: quoted-printableīenjamin Tissoires Jan. Received: from (helo=localhost)īy with esmtpsa (TLSv1:AES256-SHA:256) Received: from ()īy mx. with esmtp (Exim 4.82) H=Content-Transfer-Encoding:Content-Type:Mime-Version:From:Subject:Cc:To:Message-Id:Date īh=6t12AjWSXexoBoy43ENgiRMZVTFjgEOsVd08VaM9zq4= ī=hRdVDaS24ZhLaMh/Ztr4NlwsWrn4K1yEsQnbWONfs+Rj0hbl/OHlcLhR49pabi7RmQRxA4T2TzU2RR7N3NtisfLw0/9L9ElMy//mPJcdFsLBA19Ke1nCcPf/fyAGTP2BU4n9uoicoIqYGa5hjf4yIH+QU9VbllQWgM0sPng2y4c= X-Greylist: delayed 1186 seconds by postgrey-1.27 at ĭKIM-Signature: v=1 a=rsa-sha256 q=dns/txt c=relaxed/relaxed Received: from ( )īy mail.wl. (Postfix) with ESMTP id EFA31288BC X-Spam-Status: No, score=-7.7 required=2.0 tests=BAYES_00,DKIM_INVALID,ĭKIM_SIGNED,MAILING_LIST_MULTI,RCVD_IN_DNSWL_HI autolearn=ham version=3.3.1 X-Spam-Checker-Version: SpamAssassin 3.3.1 () on Received: by mail.wl. (Postfix, from userid 486) Received: from mail.wl. (localhost )īy mail.wl. (Postfix) with ESMTP id D1C73288BC Since libinput has largely usurped synaptics I'd think the basics would at least apply.Received: from mail.wl. (īy (Postfix) with ESMTP id E0B6813AD

0 notes
Text
Deduplicator in mailclient

DEDUPLICATOR IN MAILCLIENT UPGRADE
DEDUPLICATOR IN MAILCLIENT VERIFICATION
DEDUPLICATOR IN MAILCLIENT SOFTWARE
DEDUPLICATOR IN MAILCLIENT PROFESSIONAL
This is a multi-part message in MIME format. eM Client likewise provides a Deduplicator tool, which will find duplicates in your contacts, emails, calendar events, and jobs. A simplistic mail client that only supports. X-Asterisk-CallerIDName: YPCR Braswell EddieĬontent-Type: multipart/mixed boundary="-voicemail_188842702132051636022834" email deduplicator 452 downloads 11 MB SysTools Email Duplicate Analyzer 1.0.0.0. permission from the admin using a generated OTP transferred to the mail client. Received: (from (8.14.7/8.14.7/Submit) id w11J4RnN023476 while supporting Deduplication, the convergent encryption technique has. I underlined the most suitable items in bold here. computer hardware, computer software, or.
DEDUPLICATOR IN MAILCLIENT SOFTWARE
a practical, answerable problem that is unique to software development. Ur1H9yJacdGr91EA93TuoEyMJGk+ciw+CJM30RMqb2WO/QL6FtrWItzCk6zwlHnqCNĬD7nnKEiwSj/9E2Hkeh6M0ozNR90TQIRAiGjXXJI= software tools commonly used by programmers and is. Received: from (.net )īy (Postfix) with ESMTPS id A381530801E8ĭKIM-Signature: v=1 a=rsa-sha256 c=relaxed/simple d= īh=pljnYJnI+JWe2/sJ5Tb/7fXKiJP7PTLtQkk0C4qW79g= ī=GGnpn0rCcz+lbvz0hkx9oW2NqpMCxvbXer3Dah05oHHjUaVEWiKk9SgjY+6xQT6+J Either change or delete rule conditions to reduce the number of characters included, and then try again. Received: from ( )īy (Postfix) with ESMTPS id 6FDF21251DA Have you encountered these limitations when working with Duplicate Detection functionalities in Dynamics 365 You can include only 450 characters in the matchcode. X-Sieve-Redirected-From: from (localhost )īy (Postfix) with ESMTP id 3ACE91251E3 Received: by (Postfix, from userid 2000) Deduplication occurs so that the email only receives a single version of. with Microsoft Outlook Microsoft Outlook is an email client that can retrieve and send. Data deduplication is a feature in Windows Server 2012 and later that performs data reduction on a volume by storing one copy of data where there are. Received: from ()īy ( ) (amavisd-new, port 10024) ensures the email signature is established in the supported email client. Stellar Deduplicator for Outlook is a powerful software to remove. Tests=Īuthentication-Results: (amavisd-new) dkim=pass (1024-bit key) X-Spam-Status: No, score=-0.1 tagged_above=-999 required=4 There is not much you can ask for when it comes to email management.Delivered-To: from (localhost )īy (Postfix) with ESMTP id 363191251D7
DEDUPLICATOR IN MAILCLIENT PROFESSIONAL
With all the features it provides, you will be able to manage all personal and professional tasks, send messages directly to friends, and more. Either way, the program has a gorgeous layout that supports color coding and multiple themes.ĮM Client is more than just an email client.
DEDUPLICATOR IN MAILCLIENT UPGRADE
If you use the free version, the program only accepts two accounts, so if you want unlimited accounts, you need to upgrade to Pro. It also offers features for calendars, tasks, contacts.
DEDUPLICATOR IN MAILCLIENT VERIFICATION
It usually runs smoothly, but if you do two-step verification for the account you want to set up, it may cause you some difficulties. eM Client is a powerful email client for Windows and macOS with a clean and easy-to-use interface. It has widgets for most popular email providers, and even allows you to import from other clients such as Outlook. You can properly work with that customer by inserting your email and letting it slowly fill in all the remaining information it needs. Otherwise, copy the information below to a web mail client. In addition to letting you manage multiple email accounts, eM Client will also organize your calendar, meetings, contacts, etc., so you don’t need to think about it. We welcome your comments To open the configured email client on this computer, open an email window.

0 notes
Text
This guide will walk you through the steps to Install GitLab CE on Debian 11|Debian 10. GitLab Community Edition (CE) is an open-source application for hosting Git repositories in your own infrastructure. With GitLab you can do project planning and source code management to CI/CD and monitoring. GitLab has evolved to become a complete DevOps platform, delivered as a single application. The next sections will cover the steps to be followed to have a running GitLab CE on Debian 11|Debian 10 Linux machine. Debian 11 is currently available for general use and we’ve chosen it to host our GitLab service. In my setup I’ll use a server with the following specs: 8GB of Ram 4 vcpus 40GB Disk space Domain name: git.computingpost.com See output shared below. $ free -h total used free shared buff/cache available Mem: 7.8Gi 74Mi 7.6Gi 9.0Mi 101Mi 7.5Gi Swap: 4.0Gi 0B 4.0Gi $ grep -c ^processor /proc/cpuinfo 4 $ df -hT / Filesystem Type Size Used Avail Use% Mounted on /dev/vda1 ext4 40G 963M 37G 3% / So let’s start installation of GitLab CE on Debian 11|Debian 10 system. Step 1: Update Debian server For newly installed Debian server, update all packages and upgrade any system packages to the latest release. sudo apt update sudo apt -y upgrade sudo reboot Step 2: Install GitLab Dependencies on Debian 11|Debian 10 Once the server has been updated and rebooted, install important software packages for GitLab. All the packages are installed from default package repositories. sudo apt -y install curl vim openssh-server ca-certificates Step 3: Configure Postfix Send-Only SMTP Server GitLab should be able to send emails to you on Git activities. Configure Postfix SMTP Server using the guide below: Install and Configure Postfix as a Send-Only SMTP Server on Debian Other email solutions can be used as discussed in detail on configure an external SMTP server. Step 4: Add the GitLab CE Repository With the dependency packages installed, let’s add GitLab repository to our Debian 10 server. curl https://packages.gitlab.com/install/repositories/gitlab/gitlab-ce/script.deb.sh | sudo bash If this is successful, a positive message should be displayed. Running apt-get update... done. Installing debian-archive-keyring which is needed for installing apt-transport-https on many Debian systems. Installing apt-transport-https... done. Installing /etc/apt/sources.list.d/gitlab_gitlab-ce.list...done. Importing packagecloud gpg key... done. Running apt-get update... done. The repository is setup! You can now install packages. Step 5: Install GitLab CE on Debian 11|Debian 10 Next, install the GitLab package while changing https://gitlab.example.com to the URL at which you want to access your GitLab instance. export GITLAB_URL="http://git.computingpost.com" sudo EXTERNAL_URL="$GITLAB_URL" apt install gitlab-ce If your server has a public IP and access to the internet, you can use https and Let’s Encrypt SSL certificate. export GITLAB_URL="https://git.example.com" sudo EXTERNAL_URL="$GITLAB_URL" apt install gitlab-ce The installation will automatically configure and start GitLab at the URL provided. Whenever you change GitLab configurations on /etc/gitlab/gitlab.rb, reconfigure the application by running the following command. sudo gitlab-ctl reconfigure Step 6: Access GitLab CE Web Interface Once the installation of GitLab CE on Debian 11|Debian 10 is done, open the URL http://gitlab.example.com on your browser to finish the installation of GitLab CE. On your first visit, you’ll be redirected to a password reset screen. Provide the password for the initial administrator account and click on the Change your password button when you are finished. You will be redirected back to the login screen. Use the default account’s username root and password set to login.
The next screen should be a Welcome to GitLab page. Learn more from the GitLab documentation.
0 notes
Text
Programming Project 2 Notation Converter Solution
Programming Project 2 Notation Converter Solution
Instructions For Programming Project 2, you will implement a Deque (Double-Ended Queue) and use that data structure to write a class that can convert between the three common mathematical notation for arithmetic. The three notations are: Postfix (Reverse Polish) Notation: Operators are written after operands A B – C + == (A – B) + C Infix Notation: The standard notation we use where the operator…

View On WordPress
0 notes
Text
Organic Food Blog
The benefits of medical strawberries include improved eye brain and proper cerebrum function and relief from hypertension joint pain, gout , and other heart diseases. The significant cells and polyphenolic substances of strawberries makes them beneficial in boosting the strength of the structure, counteracting various kinds of growths, and reducing the signs of premature maturing organic food blog.
The berries, with appealing looks and great taste, have earned their spot on the list of the most loved items by a lot of people since a long time ago. Strawberries are the logical name of Fragaria however there are distinct postfixes for different varieties such as Fragaria Vesca to mean wild strawberries as well as Fragaria Orientalis for Eastern Strawberries as well as other. Strawberries grow in hedges and are among the finest natural products that can also help your overall health.
Strawberries are often referred to with European organic product and,, to a degree, they're. They were used in Roman times, and initially developed as a garden organic food in France in the 18th century. However, they were also used throughout South American societies significantly prior to that, organic health planet but because there was also a supply of strawberry in Europe the fruit is usually considered to be local to the area.
Strawberries are frequently used in a variety of food items that includes frozen jams, yogurts squashes, syrups sweet treats, prepared items as well as chocolates, and even in medicines for their delicious flavor, taste and color. Also, they can be utilized to make to create new. We are aware that all organic products particularly berries, and those with exceptional hues are full of cancer-fighting agents. This suggests that they are powerful boosts to your health as well as the protection of your organs from deadly attacks.
Nutritious Value of Strawberries
Strawberries aren't a special case to this rule; in addition to the fact that they are cancer-prevention agents They also contain a variety of supplements as well as vitamins and minerals that improve general health. They include manganese, folate, potassium and dietary fiber. They also contain magnesium. Additionally, organic food supplements it is extremely rich in Vitamin C! Together, these two segments are the reason for the amazing health benefits of strawberries. We must study these in greater detail in the section below.
Health benefits of Strawberries
What do we think about investigating further on these possible healthy benefits organic food strawberries for health in the detailed point-by-point clarifications below.
Eye Care
The main reasons behind every issue that is attributed to eye problems are caused by free radicals or a lack of certain supplements. As we age and the absence of these protective supplements, harmful free radicals or oxidants can cause significant harm to our eyes, such as dry eyes, the degeneration of optic nerves, macular degeneration vision deserts, and a broader immunity to disease too.
Cell reinforcements like flavonoidsand phenolic phytochemicals and Elagic corrosive all of which are present in strawberries, may help to keep a distance from the situation to a large extent. Another problem that the strawberries can address can be corrected is the visual burden, which refers to that the weight of the eyes. Any slight increase in this weight can be very harmful to the eyes. Strawberries can be beneficial in light of their fact they are rich in potassium, which maintains the appropriate weight read more at organic food blog.
0 notes
Text
Write a program that takes an infix expression as an input and produces a postfix expression
Write a program that takes an infix expression as an input and produces a postfix expression
C++ Write a program that takes an infix expression as an input and produces a postfix expression. Use stack to convert an infix expression into postfix expression. Include a function that evaluates a postfix expression.
View On WordPress
0 notes
Text
C1000-018 Real Exam Questions - IBM QRadar SIEM V7.3.2 Fundamental Analysis
How to prepare for C1000-018 IBM QRadar SIEM V7.3.2 Fundamental Analysis exam well? We highly recommend you to choose PassQuestion C1000-018 Real Exam Questions as the preparation materials today. The helpful and acutal C1000-018 Real Exam Questions are written by the great team, who spent a lot time and energy in IBM C1000-018 exam content. They have verified all the C1000-018 exam questions and answers, which cover the IBM C1000-018 exam objectives to ensure your success in C1000-018 IBM QRadar SIEM V7.3.2 Fundamental Analysis Exam in the first try.
IBM QRadar SIEM V7.3.2 Fundamental Analysis C1000-018 Exam
IBM Certified Associate Analyst - IBM QRadar SIEM V7.3.2 certification is intended for security analysts who wish to validate their comprehensive knowledge of IBM Security QRadar SIEM V7.3.2. These security analysts will understand basic networking, basic Security and SIEM and QRadar concepts. They will also understand how to log in to, navigate within, and explain capabilities of the product using the graphical user interface. Additionally, they will also be able to identify causes of offences, and access, interpret and report security information in a QRadar deployment.
There are 60 questions in the C1000-018 exam and you need to answer 38 questions correctly to pass this exam, the time duration is 90 minutes, you can choose English or Japanese language to give your IBM C1000-018 exam. After passing this C1000-018 exam, you will get your IBM Certified Associate Analyst - IBM QRadar SIEM V7.3.2 certification.
C1000-018 Exam Section
Section 1: Monitor outputs of configured use cases. 15% Section 2: Perform initial investigation of alerts and offenses created by QRadar. 35% Section 3: Identify and escalate undesirable rule behavior to administrator. 20% Section 4: Extract information for regular or adhoc distribution to consumer of outputs. 17% Section 5: Identify and escalate issues with regards to QRadar health and functionality. 13%
View Online IBM QRadar SIEM V7.3.2 Fundamental Analysis C1000-018 Free Questions
To provide insight into why QRadar considers the event to be threatening, what does QRadar add to the Offense that users cannot edit or delete? A.Annotations B.Attack path C.Location D.Source IP Answer: A
An analyst has been assigned a task to modify a rule in such a manner that Source IP of the triggered Offense from this rule should be stored in a Reference set. Under which section of the rule wizard can the analyst achieve this? A.Rule Response B.Rule Action C.Rule Test Stack Editor D.Rule Response Limiter Answer : C
An analyst has been assigned a number of Offenses to review and a new event occurs. review and manage. While reviewing an inactive offense, a new event occurs. Which statement applies to the Offense? A.The event is added in a new Offense that is created. B.The event is added to the Offense and the status is changed to Dormant. C.The rule that created the Offense is temporarily halted. D.The event is added to the Offense and the status is changed to Active. Answer : B
The SOC team complained that they have can only see one Offense in the Offenses tab. space of 10 minutes, but the analyst How can the analyst ensure only one email is sent in this circumstance? A.Configure the postfix mail server on the Console to suppress duplicate items B.Ensure that the Rule Action Limiter is configured the same way as the Rule Response Limiter. C.Add a Response Limiter to the Rule, configured to execute only once every 30 minutes. D.Disable Automated Offense Notification - by email, in Advanced System Settings. Answer : A An analyst is noticing false positives from a single IP on a specific offense. How can the analyst tune the event rule to eliminate these false positives? A.Add the rule test 'AND when IP address equals' to the bottom of the test list of the rule. B.Add the rule test 'AND NOT when the offense is indexed by one of the following IP addresses'. C.Add the rule test 'AND NOT when IP address equals' to the bottom of the test list of the rule, D.Add the rule test 'AND when IP address equals' to the top of the test list of the rule. Answer : C
0 notes